Azure SaaS for codeBeamer and Retina
What is this document about?
This document describes how to set up Intland-hosted SaaS solutions in a matter of minutes. We provide details on how the deployment architecture looks like and how can we ensure the highest level of security for your data.
Deployment process
Please navigate to our trial page and fill the trial registration form. After this you will receive a confirmation email which allows you to verify your email address. With a confirmed email address, the trial registration is active and you will get a new standalone codeBeamer/Retina instance, which is only available to you. In just a few minutes, you will be able to log in and start using the product with your registration details.
and fill the trial registration form. After this you will receive a confirmation email which allows you to verify your email address. With a confirmed email address, the trial registration is active and you will get a new standalone codeBeamer/Retina instance, which is only available to you. In just a few minutes, you will be able to log in and start using the product with your registration details.
Deployment architecture
The solution is hosted on Azure, using native resources such as the Azure MySQL DB and Azure Kubernetes cluster. All keys are stored securely in hardware security modules (Azure key vault with HSM), so only your instance can use them. For safety reasons we cannot expose the actual architecture, in case of questions, feel free to contact us.
Security
The security of your data is our number one priority, so we apply all best practices from the open field to ensure it. We only allow HTTPS access to your instance from the open network, it is complete separated from other deployments, and even our administrators can't reach your data thanks to the secure virtual network architecture. Your data is only available on the instance which you are using, everything is encrypted at rest and also during traffic. All instances have separate databases, meaning that they cannot reach any other instance running in the same cloud. For more details on security considerations, feel free to reach out to us.
All deployments are located behind firewalls, meaning that all traffic is filtered and we can block unwanted access to the instances.
Advanced security, networking
If you want to make your instance invisible from the open network, we have extra configuration which allows only limited access from outside networks to this instance. We have several custom networking use-cases, where the instance could not have any public IP addresses, this can be easily configured.
In case you want to host the instance under your own Azure subscription without any external connections, this use case is covered in another document in this tree.
Azure SLA
Service level agreements from Azure can be fond on this LINK . The used services are AKS, Azure DB for MySQL, Azure Premium Keyvault, Standard Load Balancer, Azure Firewall, Network Security Groups, Premium File Share. For more information please contact us.
. The used services are AKS, Azure DB for MySQL, Azure Premium Keyvault, Standard Load Balancer, Azure Firewall, Network Security Groups, Premium File Share. For more information please contact us.
Configuring LDAP/Active Directory
See  LDAP/Active Directory configuration instructions.
LDAP/Active Directory configuration instructions.
Migrating your data to Azure cloud
The easiest way to migrate your data to Azure cloud is either:
- Do a mysql backup/dump and import to Azure
- Or export using codeBeamer's project export and import on Azure server. Note that project export/import has few
 known limitations!
known limitations!
IT Service Continuity
For all of our instances we have 99.9% for the VM running them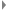 . The load balancers responsible for routing have 99.99% availability. If anything happens in an instance, it is automatically restarted with a clean cache with the same DB and file share connections, a restart time is around 1 minute including the rescheduling.
. The load balancers responsible for routing have 99.99% availability. If anything happens in an instance, it is automatically restarted with a clean cache with the same DB and file share connections, a restart time is around 1 minute including the rescheduling.
Backup and disaster recovery on Azure cloud
The Azure MySQL server is backed up for 35 days for all changes. We create consistent (storage+MySQL DB) daily backups from 3:00AM to 5:00AM every day and keep them for a year. This ensures a reliable disaster recovery solution which allows us to guarantee failsafe operation.
Disaster recovery is done by our devops team and can be done in a few minutes depending on the instance size. Backups are kept encrypted (2x) on Azure Blob storage in cold tier, they are available for transfer 24/7. Backup passwords are kept in customer-specific key vaults available only for the customer. Snapshot and restore mechanism is fully automated, so no manual interaction is required for the process. The Blob storage is only available on private network.
Recovery Point Objective (RPO)
As backup is done every day is 4AM the worst case incident may occur at 3:59AM next day meaning a worst-case 24 hours RPO. In general, we can approximate the RPO with less hours, as servers are usually not used at night. If changes are only made in the MySQL database only, our RPO is 1 second, we can restore any previous state of the database from the last 35 days (this is only possible if there are no filesystem changes).
Recovery Time Objective (RTO)
Disaster recovery RTO is 4 hours for general cases (few minutes for small instances), which means we restore the exact state of the system before disaster on the server. In extreme cases (huge databases) it can take at most 16 hours to complete the full recovery procedure. We can back up any snapshot from the previous year automatically.
Azure security certifications
Azure cloud security management is ISO/IEC 27001, our deployment uses only built-in security solutions from Azure which are properly validated. We apply all best practices from the open field for running the deployments as secure as possible.
is ISO/IEC 27001, our deployment uses only built-in security solutions from Azure which are properly validated. We apply all best practices from the open field for running the deployments as secure as possible.
Azure availability regions
Azure regions are listed here . The selected region needs to have premium file shares, Azure DB for MySQL and AKS enabled. For this reason we recommend using West Europe or Germany West Central if you are located in Germany, as this regions are tested and provide the best experience. We support deployments with local clusters in Americas and APAC regions to ensure the best connection between the server and end users.
. The selected region needs to have premium file shares, Azure DB for MySQL and AKS enabled. For this reason we recommend using West Europe or Germany West Central if you are located in Germany, as this regions are tested and provide the best experience. We support deployments with local clusters in Americas and APAC regions to ensure the best connection between the server and end users.
Azure Security Compliance
The deployment is compliant to the default Azure security standards, audits are performed frequently to maintain 100% compliance state for the SaaS cluster. All policy audits are evaluated one by one in case of exemptions and the compliance of the system is guaranteed by automation.
![[!1600850277157.png!]](/cb/displayDocument/1600850277157.png?doc_id=11789911&version=1&history=false¬ification=false)